
Every time you visit a website that starts with HTTPS, you’re using a certificate authority. But what exactly is a CA and how does it make your transactions and communications more secure?
Certificate authorities (CA) are a critical part of the internet. If CAs didn’t exist, you wouldn’t be able to shop, pay taxes, or do banking online because the internet would be insecure. (Your web browser is actually using a certificate authority right now.)
But what is a certificate authority, exactly? What does a certificate authority do? And how do certificate authorities work?
Let’s hash it out.
What Is a Certificate Authority (CA)?
A certificate authority, also known as a certification authority, is a trusted organization that verifies websites (and other entities) so that you know who you’re communicating with online. Their objective is to make the internet a more secure place for organizations and users alike. This means that they play a pivotal role in digital security.
If that sounded slightly nebulous or confusing, let’s use an example to explain what a certificate authority is. Let’s say you’re visiting your bank’s website, bbt.com:
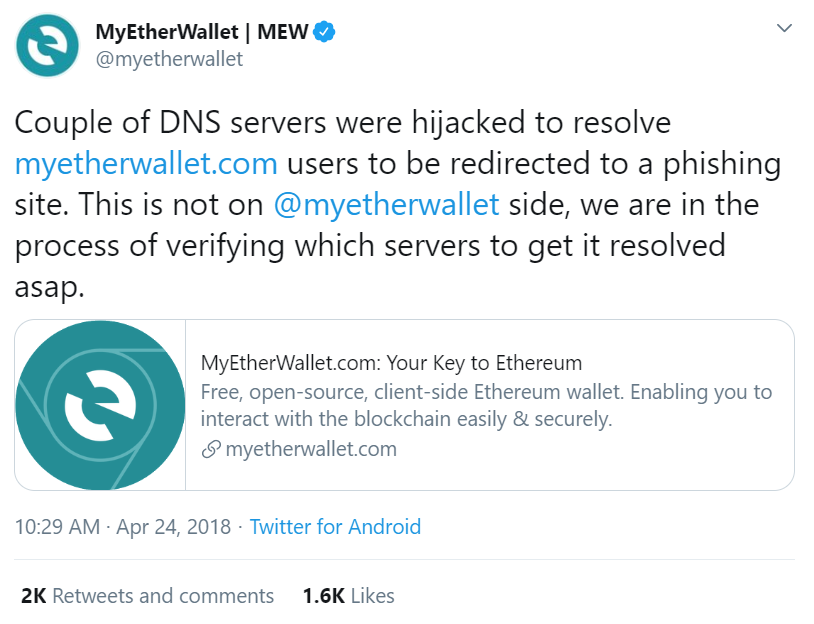
If you’re familiar with how the internet works, you know that things are not always as they seem. The website looks like bbt.com, and the domain says that it’s bbt.com… but how do you know that you’re actually connected to a server that’s run by BB&T? How do you know it’s not a hacker who built a website that looks just like bbt.com? For hacker geniuses, that’d be pretty easy to do — here’s a recent example of this kind of attack:
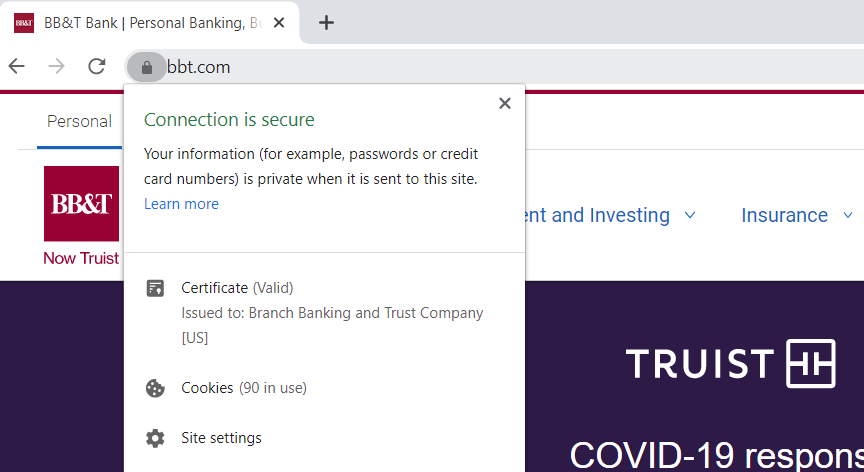
So how do you know you’re connected to the real website? That’s a certificate authority’s job — they verify websites/organizations so that you know who you’re communicating with online. (This way, you don’t accidentally send your credit card number to a hacker in Timbuktu.) So, if we look at the SSL/TLS certificate details for bbt.com, we can see that the website has been verified by DigiCert Inc. This means that DigiCert is the certificate authority that verified BB&T/bbt.com so you can be 100% confident that you’re connected with the official BB&T website:

Certificate Authorities Are Like Passport Authorities for the Internet
If you’ve ever gotten a passport to travel internationally, you probably remember the verification process that you went through to prove that you are who you claimed to be. (It probably included some legal papers, photo ID, and maybe fingerprints.)
Once you got your passport, you could use it to prove to anyone that you’re really you. (Even if they’d never met you before.)
Certificate authorities are like that — but for websites and online activities. Just like the passport office, a certificate authority charges a small fee to complete the verification process and issue the certificate. In this case, after they verify a website (or organization), they issue what’s known as a digital certificate. This digital file enables organizations, websites, or other entities to prove who they are — that they’re the real deal.
So how does all of this work? After all, websites don’t have actual passports, and I don’t remember scanning any passports when I visit my bank’s website…
Let’s dive into this topic in more detail.
How a Certificate Authority Works: The Technical Details
Certificate authorities are one of the integral parts that make up a larger system called public key infrastructure, or PKI for short. If you want to read more about how it works, see our article that offers a deep dive on how PKI works. But for now, let’s just give a quick overview before moving on. To keep things simple, we’ll keep talking about how PKI works with websites.
When you go to a website and see the padlock (or the security details like we showed above for bbt.com), the technology that’s enabling that is an SSL certificate (or, more accurately, a TLS certificate, but you can use either term).
SSL/TLS certificates are based on PKI, and there are a few key parts that need to be in place for the SSL certificate to work:
- A digital certificate (for example, an SSL/TLS certificate) that proves the website’s identity.
- A certificate authority that verifies the website and issues the digital certificate.
- A digital signature that proves the SSL certificate was issued by the trusted certificate authority.
- A public key that your browser uses to encrypt data sent to the website.
- A private key that the website uses to decrypt the data sent to it.
Let’s take a look at this visual. It helps to break down the process of how PKI works in website security and the role that CAs play in it:
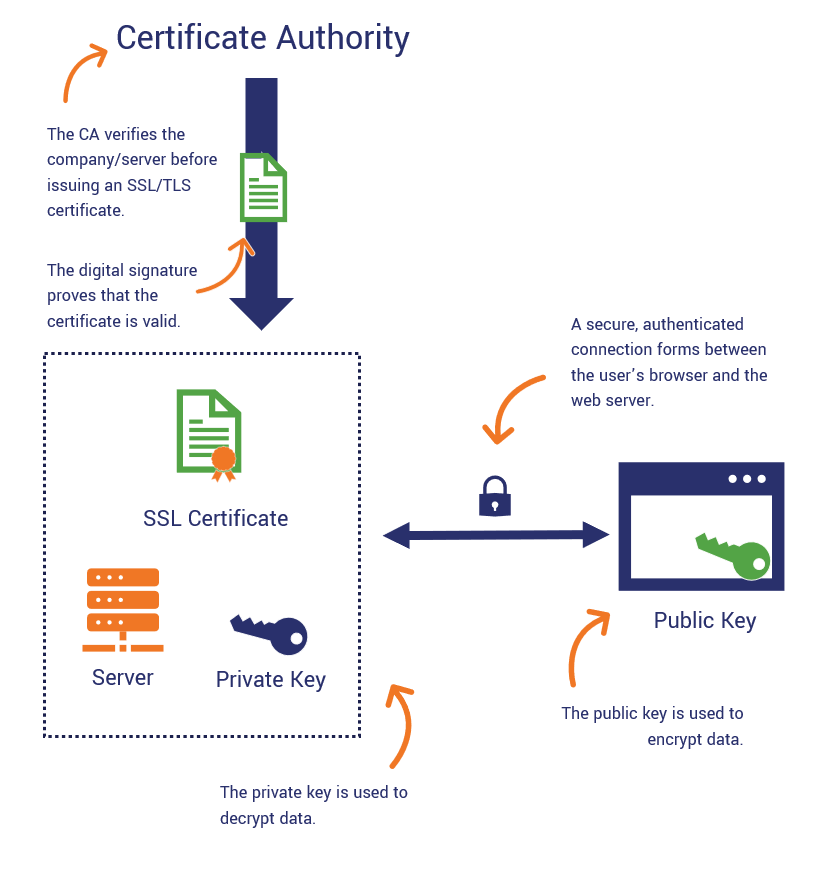
As you can see there, the certificate authority is at the top of the process. That’s because once someone requests a certificate, everything trickles down from the CA after that.
What Does a Certificate Authority Do? Breaking Down the Functions of a CA
As we mentioned, commercial certificate authorities are integral to public key infrastructure. What they do is:
- Vet domain names, individuals and organizations to validate their identities through official records.
- Issue digital certificates that authenticate servers, individuals and organizations (establishing trust).
- Maintain certificate revocation lists that indicate when certificates become invalid prior to their expiry dates. (We’ll speak more to this later in the article.)
Let’s dive into the specific functions that they perform to explain this a bit more.
Verification
The process starts when a website approaches a certificate authority to obtain a digital certificate. The certificate authority completes a verification process, depending on the type of certificate requested:
- Domain validation — The certificate authority verifies that the requestor is the legitimate manager of the domain/website in question. That’s it. Needless to say, this means that domain validation is the bare minimum in terms of validation.
- Organization validation — The certificate authority not only verifies that the domain information is legitimate, but it goes a step further and performs basic business validation. The OV process involves a human element. Basically, the CA reviews information that the certificate requestor provides and also researches additional information (using third-party records and sources) to ensure the organization is legitimate.
- Extended validation — This is the most thorough level of business validation. In this one- to five-day validation process, the CA takes an extensive look at the requestor’s organization. They go above and beyond the requirements of the OV validation process to ensure that your organization truly is legitimate.
By requiring individuals and organizations to verify themselves, the CA is able to offer greater assurance that the requestor’s website is real.
Digital Certificates
Certificate authorities bring identity into the picture through certificate authentication. And this is what helps the website to establish trust with your browser.
Although we’ve only really talked about one type so far (SSL/TLS certificates), there are actually multiple categories of digital certificates that CAs issue — and each plays a different role within PKI. In some cases, there are multiple types of digital certificates within each category. All of these certificates are known as X.509 digital certificates because X.509 is the technical standard they all comply with.
SSL/TLS Certificates
SSL/TLS certificates (aka website security certificates) are what we’ve been talking about so far. These certs are what facilitate the secure, encrypted connections that take place between a user’s browser and your web server. (Remember that padlock icon we pointed out earlier? Yeah, these certs are what make that possible.)
These certificates are what eliminate the “not secure” warnings in the URL bar and the “your connection is not private” warning messages that browsers display for insecure websites. For example, here’s what it looks like in Chrome when no SSL/TLS certificate is installed (or if there is one but it’s improperly configured):
Types of SSL/TLS Certificates
SSL/TLS certificates are divided by their validation levels and functionalities:
- Validation levels: These are the domain, organization and extended validation types that we discussed a little bit ago.
- Functionalities:
- Single domain certificates — As the name would implies, these types of SSL/TLS certificates secure an individual domain. (This includes both the WWW and non-WWW versions of the domain.)
- Multi-domain certificates — These certificates allow you to secure multiple domains and subject alternative name (SAN) domains under a single certificate. (SANs are alternative host names, common names, IP addresses, etc.)
- Wildcard certificates — The term wildcard refers to subdomains. So, a wildcard SSL/TLS certificate is one that secures an unlimited number of subdomains for one domain under a single certificate. (For example, you may see the subdomain info listed with an asterisk, like *.bbt.com or *.thesslstore.com.)
- Multi-domain wildcard certificates — These certificates are kind of the best of both worlds. Not only do they enable you secure multiple domains under a single certificate, but they also allow you to secure as many subdomains as you want, too. Multi-domain wildcards offer the most in terms of versatility.
Code Signing Certificates
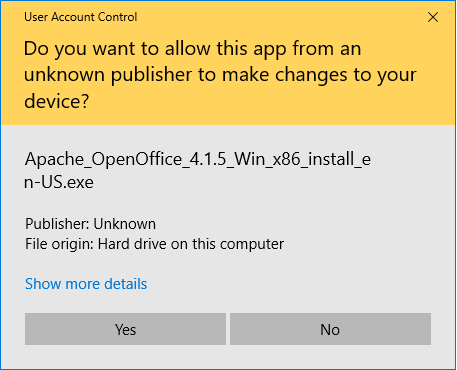
Developers and publishers use these types of certificates to digitally sign their code to ensure its integrity. This enables users to tell whether it’s been tampered with since it was signed originally. It also helps you to authenticate yourself or your organization by showing that it was you who actually signed it.
It helps you to avoid ugly warning messages like this:
Email Signing Certificates
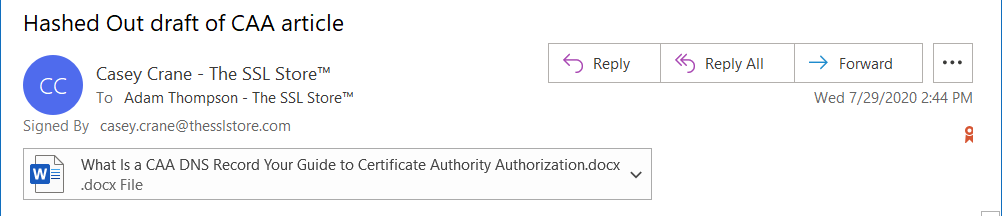
Email signing certificates are useful for authenticating individuals and clients to web servers. These certs are also known as S/MIME certificates, personal authentication certificates, client authentication certificates, etc.
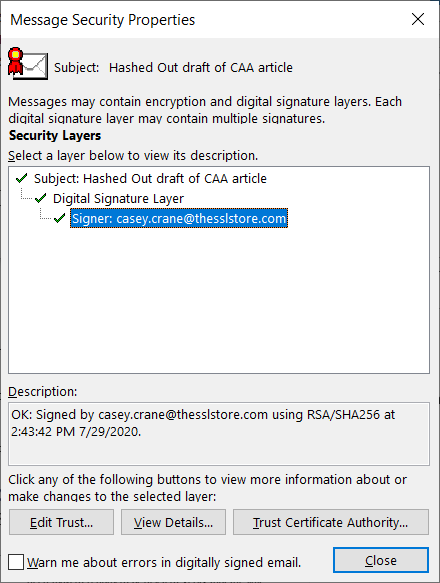
This is how an email displays when it’s signed with an email signing certificate:
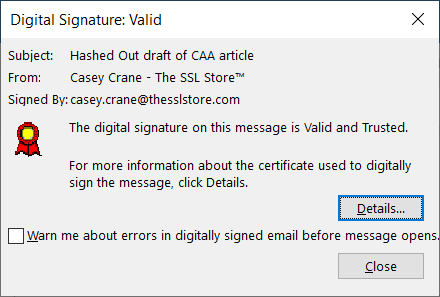
If you dig a little deeper by clicking on the ribbon on the right, it offers more information that attests that the email genuinely came from my account. (More specifically, from my device’s email client.)
Document Signing Certificates
These certificates are useful for authenticating the document creator and validating the integrity of the document itself.
The way that a certificate authority gives credence to those individual certificates is by issuing root certificates that other certificates link back to. This is what we call the chain of trust (we’ll discuss that more in depth shortly).
Digital Signatures
A certificate authority applies something called a digital signature to the digital certificate. In simple terms, the digital signature:
- Proves that the certificate was issued by the trusted certificate authority.
- Validates that…
