
The adoption of cloud services gives elasticity to the enterprise, but it can also stretch the limits of traditional security protections and leave organizations more vulnerable.
Cloud services from Microsoft and third parties help enterprises get work done, but they also present potential problems for administrators and security teams that lack the visibility into these SaaS apps. IT workers need a way to track user activities, control sensitive information and prevent malware infections that originate from these cloud services. Microsoft Cloud App Security is a cloud access security broker (CASB) with a suite of tools to keep shadow IT in check, detect unusual activities and ensure the organization stays in compliance with industry regulations. This cloud-based security product detects potential threats from inside and outside the organization, identifies and blocks risky activities and applications, and gives IT insights into the cloud apps and services used by employees.
Protection from cloud-based threats can be tricky and, in many cases, it’s not an option to use a third-party app to secure applications in the Microsoft-hosted environment. In these cases, administrators must see what Microsoft offers to monitor and protect against external and internal threats. While Microsoft does provide several built-in protections for attacks against its network, the organization’s IT staff is responsible to monitor and protect the areas that include the physical and application layers, identity, compliance, threat protection and access control.
What a cloud access security broker does
There are four key functions of a CASB that make it a must-have for organizations that use both Microsoft-based services, such as Office 365, and third-party products, such as Google Workspace and Dropbox.
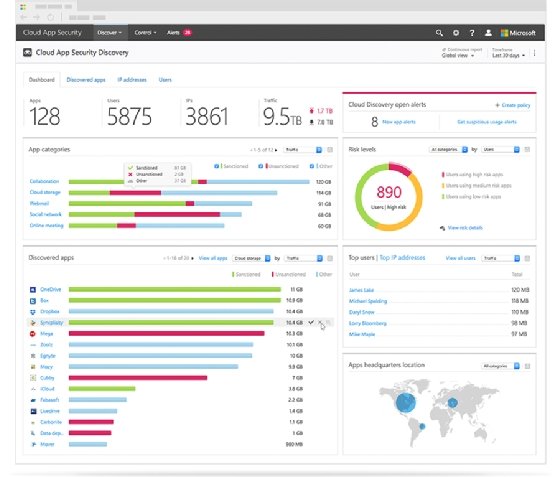
- Cloud monitoring and activity reporting. The Microsoft CASB platform has direct access to many of the behind-the-system user activities that include authentication, OneDrive for Business or SharePoint Online access, and other end-user activities in the cloud suite. With this type of exclusive access, the Cloud App Security platform delivers meaningful reports to the administrators and insights into the interactions end users have with the services across Office 365.
- Activity analysis and abnormal behavior detection. A CASB collects data from logs and user activities and employs several algorithms to find and report on abnormal activities in the system based on built-in policies. Some of Cloud App Security’s detection capabilities include mass downloads by a user, activity from anonymous IP addresses, ransomware activity and leaked credentials.
- Rule-based engine to alert or to take actions. Cloud App Security features built-in policies to automatically handle threats and suspicious activities, but the system lets administrators create their own set of rules and specifications. These policies fall into six types of policies: access, activity, app discovery, cloud discovery anomaly detection, OAuth app and session policy. Administrators receive an email or SMS alert when an activity meets some of the rules.
- Connecting the dots and integrating with other systems. Protection in Cloud App Security is not exclusive to Microsoft services. Microsoft documentation claims its cloud-based security product works with more than 16,000 SaaS apps. Microsoft offers single sign-on (SSO) services to let customers connect to third-party SaaS applications, such as Salesforce and Workday, using their Microsoft credentials. Through this access, Cloud App Security reports on authentication activities against those SaaS apps. Cloud App Security features integrations capabilities through its Cloud Discovery component to connect the security product to network appliances, such as firewalls from vendors including Barracuda, Check Point, Cisco, Menlo Security and SonicWall, and use the traffic log information to provide insights around app usage.
Some Microsoft subscriptions include Cloud App Security
There are several Office 365/Microsoft 365 plans with licensing for Microsoft Cloud App Security, including:
- Microsoft 365 E5
- Microsoft 365 E5 Security
- Microsoft 365 E5 Compliance
- Enterprise Mobility + Security E5
Microsoft also offers a standalone Cloud App Security per-user license that includes all the product features with no limits on the number of apps protected for each user.
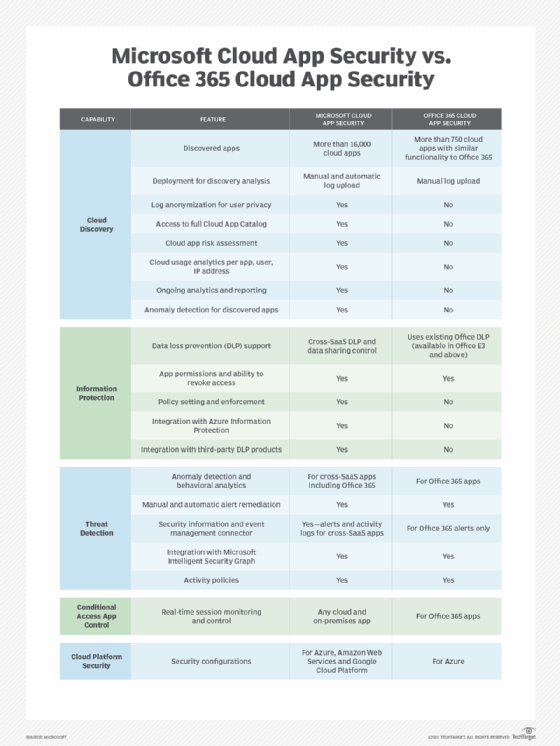
Cloud App Security vs. Office 365 Cloud App Security
Microsoft offers a limited set of Microsoft Cloud App Security features in some of the tiers on its cloud collaboration platform that it calls Office 365 Cloud App Security.
Much of the missing functionality falls under the Cloud Discovery feature set, including cloud app risk assessment, access to the full Cloud App Catalog and automatic log uploads for discovery analysis. Also missing on these lower tiers are certain Information Protection features, including policy setting and enforcement, and the ability to connect with third-party data-loss prevention products.
Microsoft provides Office 365 Cloud App Security to the following plans: Microsoft 365 Education A5, Office 365 A3 (student use benefit SKU), Office 365 A5 (student use benefit SKU), Microsoft 365 Education A3 (student use benefit SKU) and Microsoft 365 Education A5 (student use benefit SKU).
Subscriptions that are not eligible for Office 365 Cloud App Security are Office 365 Education A1, Office 365 Education A3, Office 365 Education A5 and Microsoft 365 Education A3.
Administrators must plan compliance requirements
While Microsoft Cloud App Security comes with default policies and rules administrators can deploy immediately, it is highly recommended the IT team meets with the compliance team to determine how to use the service to fulfill with the organization’s requirements.
This coordination helps define the types of restrictions, content classifications and alerts administrators must put in place for information and services used by end users.
- Define the integrations. Cloud App Security offers two types of integrations to collect traffic logs and application sign-ins. IT must determine if the firewall is compatible with the platform and if the SaaS apps offer support for Microsoft SSO.
- Create standard operating procedures to review and respond to alerts. Incident response is just as critical as the detection of a security event. Once administrators define the policies the business needs, IT must establish rules of engagements and standard operation procedures related to the frequency of dashboard reviews and response to the types of alerts sent via email and SMS.
