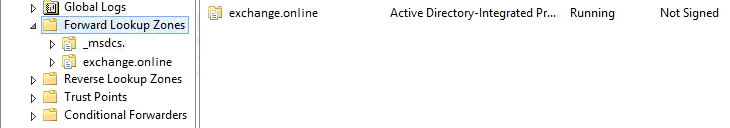This article will help to fix the below errors for MS Exchange 2016/2019
I. Certificate error “name on the security certificate is invalid or does not match the name of the site”
II. Out of Office not working
III. Make Internal URLs and External URLs the same
IV. Address book download issue
Most administrators don’t check the complete URLs that Exchange uses for serving MAPI clients or they miss URLs required to set and add certificate names after installing Exchange Server.
Below are fixes for those errors.
Note: Replace “exchange.online” with your domain name in all the examples below.
1. First make sure you have a Forward lookup zone for your domain in your internal DNS server, e.g. exchange.online (like mine in the screenshot).
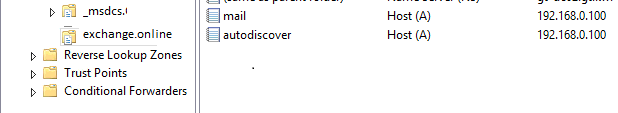
2. Then create the below A records in the newly created zone that point to the exchange CAS/HUB server IP or load balancer IP if you have one (as in the screenshot):
a) autodiscover.exchange.online
b) mail.exchange.online (common name)
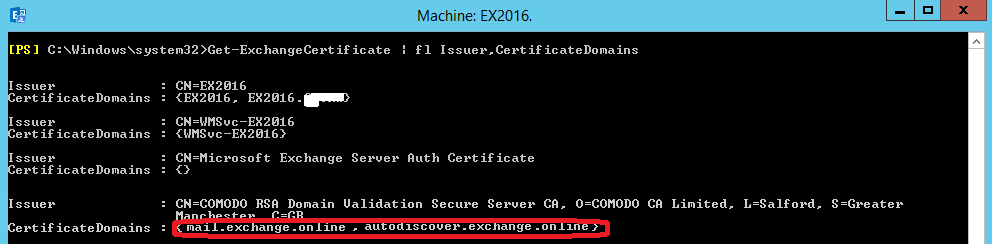
3. Then make sure you have all the required names added as SANs in your SSL Certificate. The below names should be present for a single domain exchange:
a) mail.exchange.online (common name)
b) autodiscover.exchange.online
The following command will list your SANs/names in the certificate:
Get-ExchangeCertificate | fl Issuer,CertificateDomains3.1 If you have multiple domains you have to add below SANs to your SSL Certificate:
a) mail.exchange.online (common name1)
b) autodiscover.exchange.online
c) autodiscover.exchange2.online
d) autodiscover.exchange3.online
OR
3.2 You can have one common name and one autodiscover name in the certificate and redirect all the common names to commonname.exchange.online and redirect all autodiscover to autodiscover.exchange.online.com as below:
a) mail.exchange.online (common name1) —-> A record points to Exchange server IP
b) autodiscover.exchange.onilne ——> A record points to Exchange server IP
c) autodiscover.domain2.com SRV record to redirect to autodiscover.domain1.com as below
Name: @
Service: _autodiscover Do not for to add “_” at the beginning.
Protocol: _tcp Do not for to add “_” at the beginning.
Target: autodiscover.domain1.com Outlook will be redirected to this name.
Priority: 10
Weight: 10
Port: 443
Name: All you need here is the @ symbol. This will default the record to the parent domain. In our case it will append domain2.com creating a complete record of _autodiscover._tcp.domain2.com.
Service: Enter _autodiscover. Be sure to include a single underscore in front of it. By design this is one of the names the Outlook client looks for.
Protocol: Enter _tcp. Be sure to include a single underscore in front of it. By design autodiscover requests are performed over TCP connections.
Target: This is where we want our Outlook clients redirected. This has to be a name that exists on our SSL certificate. In our case autodiscover.domain1.com
Priority: If you only have one autodiscover SRV record then it really doesn’t matter what you enter here. This is for high availability. The lowest priority number will always be used first. If it is unavailable the next lowest number will be used and so on. In our case we only have one record, so we just went with 10. But we could just have easily made it 0 or 100.
Weight: Weight is used for load balancing multiple SRV records. Should you have two SRV records with the same priority, then weight is factored in. A higher value in weight means it is preferred and more connections are sent to it. In our case we only have a single SRV record so it does not matter what we enter here. We went with 10 again.
Port: All connections will be over HTTPS. This is port 443.
4. Make sure IIS is enabled and the third party certificate installed.
Type “Get-ExchangeCertificate” in Exchange Management Shell to see if IIS is enabled.
Exchange 2016 Shell
Before services enabled
Use the command shown below to enable the services. You can change the services according to your requirement. but IIS is mandatory.
Enable-ExchangeCertificate -Services IMAP, IIS, SMTP -thumbprint 896B74B25F7EBF330C93E56DA2A76CFC6A7
After services enabled
Exchange 2016 EAC
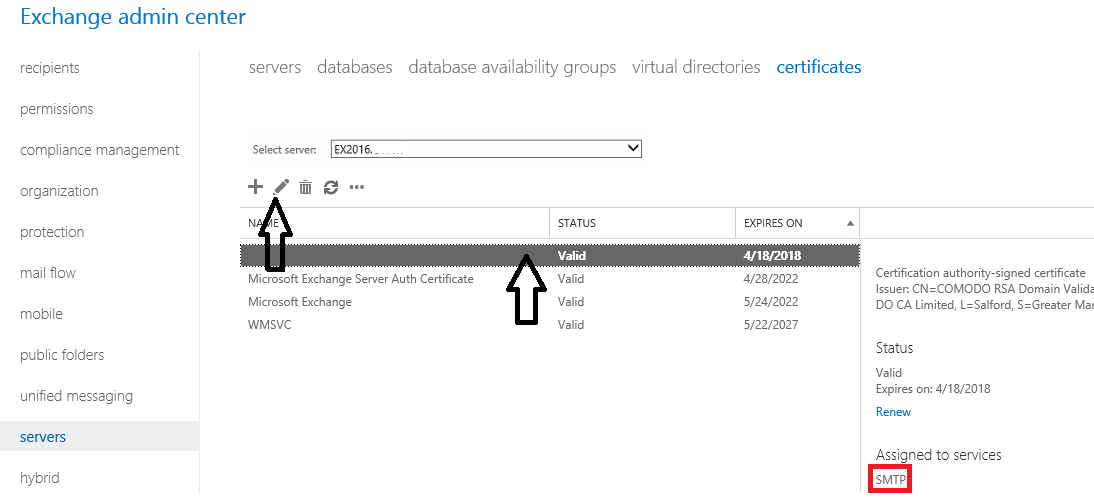
You can assign and enable service certificates in Exchange 2016/2019 from the EAC. Below are the steps with screenshots showing how to enable and assign services:
a) Click on the imported third party certificate and click the “Edit”  button
button
b) Click on Services
c) Select SMTP and IIS. If you’re also using POP and IMAP, select them as well.
You can read this TechNet article for more information on how to assign services to certificates in Exchange 2016/2019.
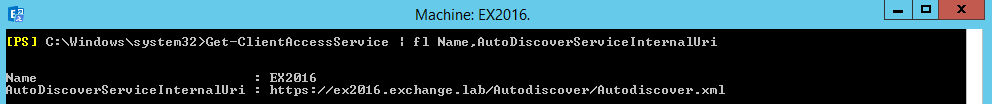
5. Enter the below command in Exchange Management Shell to see if the Autodicover URLs are set.
Get-clientAccessService | fl Name,AutoDiscoverServiceInternalUri
If you see the default URLs set by exchange installation (as above) use the below command to set it to the same as external.
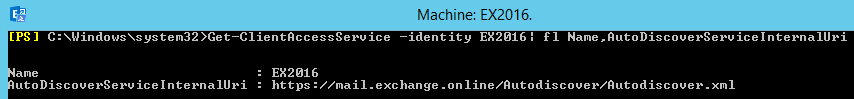
Set-ClientAccessService -Identity EX2016 -AutoDiscoverServiceInternalUri "https://mail.exchange.online/autodiscover/autodiscover.xml"
You should see as in the screenshot below after running the command again.
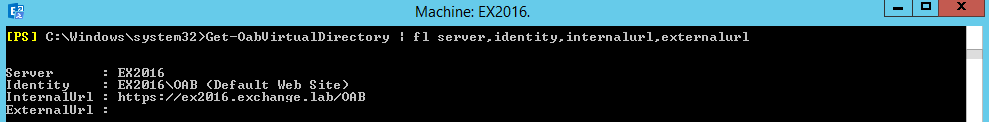
6. Enter the below command in Exchange Management Shell and see if the offline address book URLs are set.
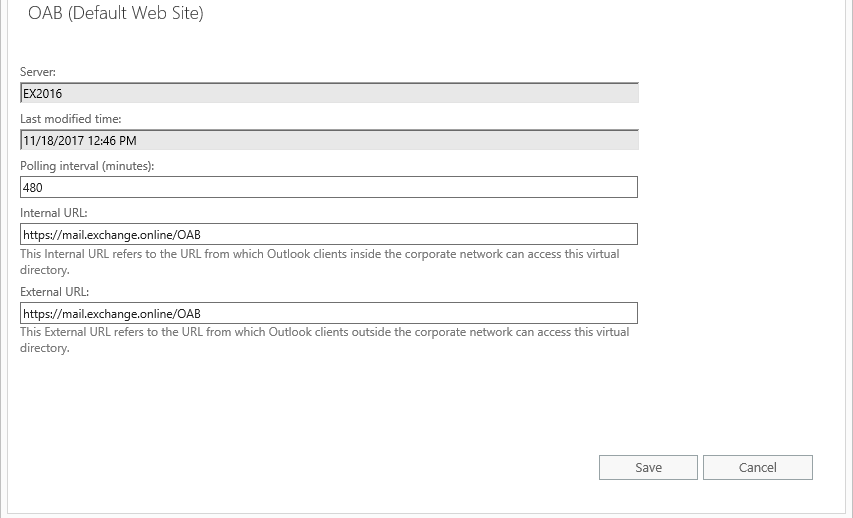
Get-OabVirtualDirectory | fl Server,Identity,internalurl,externalurl
If you see the default URLs set by exchange installation (as above) use the below command to set it to the same as external.
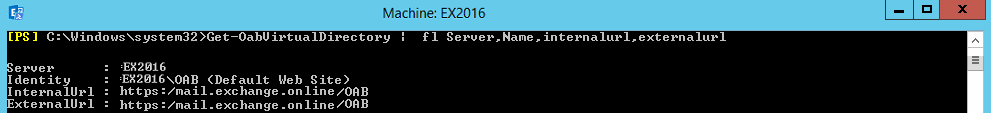
Set-OabVirtualDirectory -Identity "EX2016oab (default web site)" -InternalUrl "https://mail.exchange.online/oab" -ExternalUrl "https://mail.exchange.online/oab"
You should see the as in the screenshot below after running the command again.
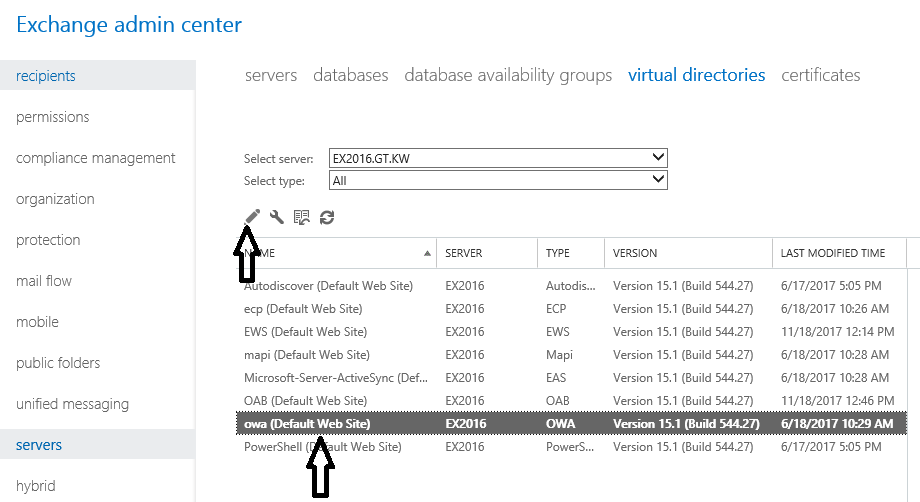
a) In Exchange 2016/2019 OAB URLs can be set from the EAC. Click on “OAB (Default Web site)” and click the “Edit”  button.
button.
b) Enter the external and internal URLs with the same value (i.e. external name) and click “Save”.
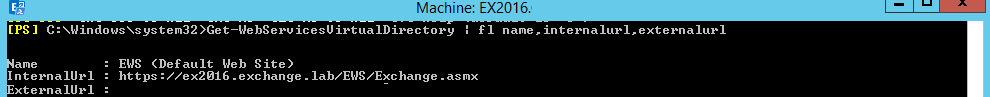
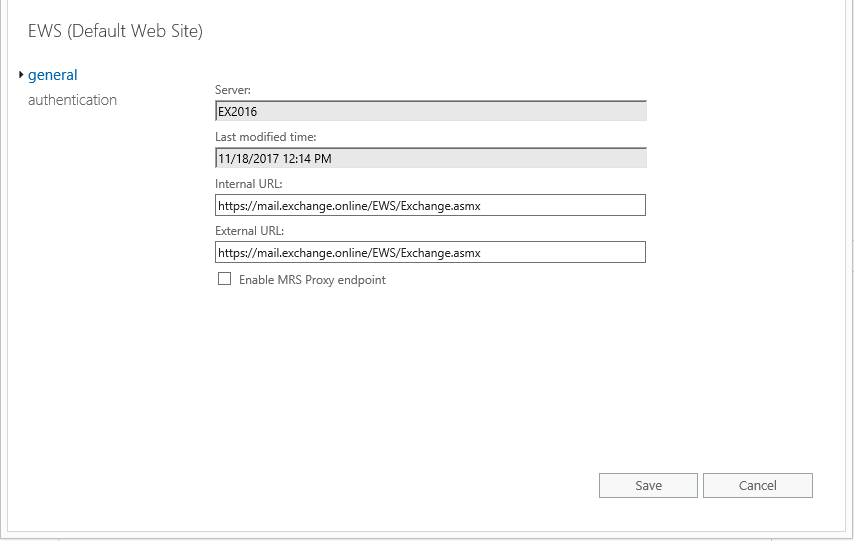
7. Enter the below command in Exchange Management Shell to see if the Exchange Web Services’ URLs are set.
Get-WebServicesVirtualDirectory | fl Server,Identity,internalurl,externalurlIf you see the default URLs set by the Exchange installation (as above), use the below command to set it to the same as the external.
set-WebservicesVirtualDirectory -Identity "EX2016EWS (default web site)" -InternalUrl "https://mail.exchange.online/EWS/Exchange.asmx" -ExternalUrl "mail.exchange.online/EWS/Exchange.asmx"You should see the following result after after running the command again.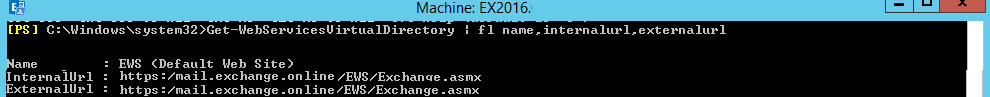
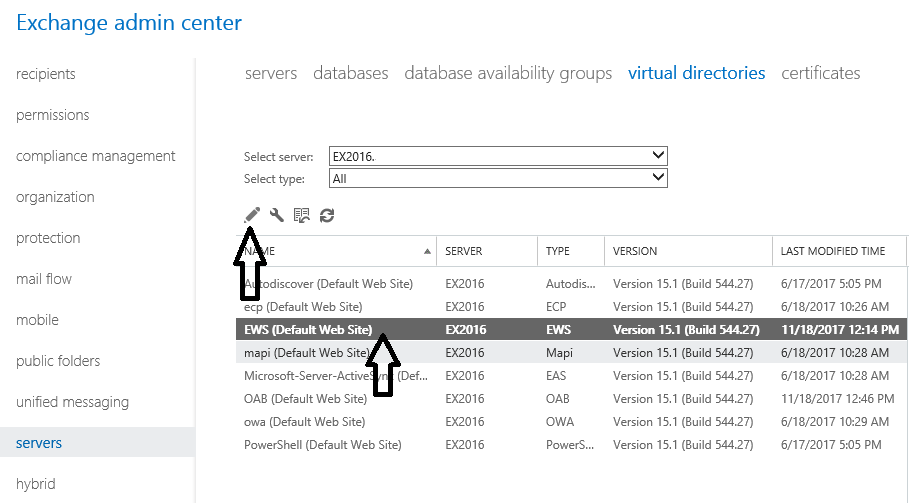
a) In Exchange 2016/2019 the EWS URLs can be set from the EAC. Click on “EWS (Default Web site)” and click the “Edit”  button.
button.
II. Enter the external and internal URLs with the same value (i.e. external name) and click “Save”.
8. Enter the below command in Exchange Management Shell to see if the Mapi URLs are set.
Get-MapiVirtualDirectory | fl Server,Identity,internalurl,externalurlIf you see the default URLs set by the Exchange installation (as above), use the below command to set it to the same as the external.
set-WebservicesVirtualDirectory -Identity "EX2016mapi (default web site)" -InternalUrl "https://mail.exchange.online/mapi" -ExternalUrl "mail.exchange.online/mapi"You should see the following result after running the command again:
a) In Exchange 2016/2019, the mapi URLs can be set from the EAC. Click on “mapi (Default Web site)” and click the “Edit”  button.
button.
II. Enter the external and internal URLs with the same value (i.e. external name) and click “Save”.
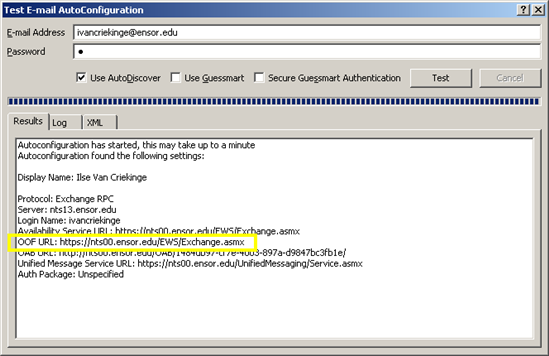
9. On a client workstation; Check to see that the Out of Office URL is correct in a client’s Outlook.
Press Ctrl and right-click on the Outlook icon located in your system tray, then select “Test E-mail AutoConfiguration”.
Enter the email address and password for the mailbox you have opened. Since we are not using POP3 or IMAP, there is no reason to leave the Guessmart checkboxes checked.
After clicking Test, look for the the URL used to configure OOF (as indicated below)
Please reset IIS using the command below (Optional but recommended).
iisreset /noforce
Now you should have all your errors cleared.
I have written articles to cover the over versions of Exchange (see below):
To clear certificate errorand set URLs in Exchange2007.
To clear certificate errorand set URLs in Exchange2010.
To clear certificate error and set URLs in Exchange2013.
Fix for Exchange server 2016/2019 certificate and related issues