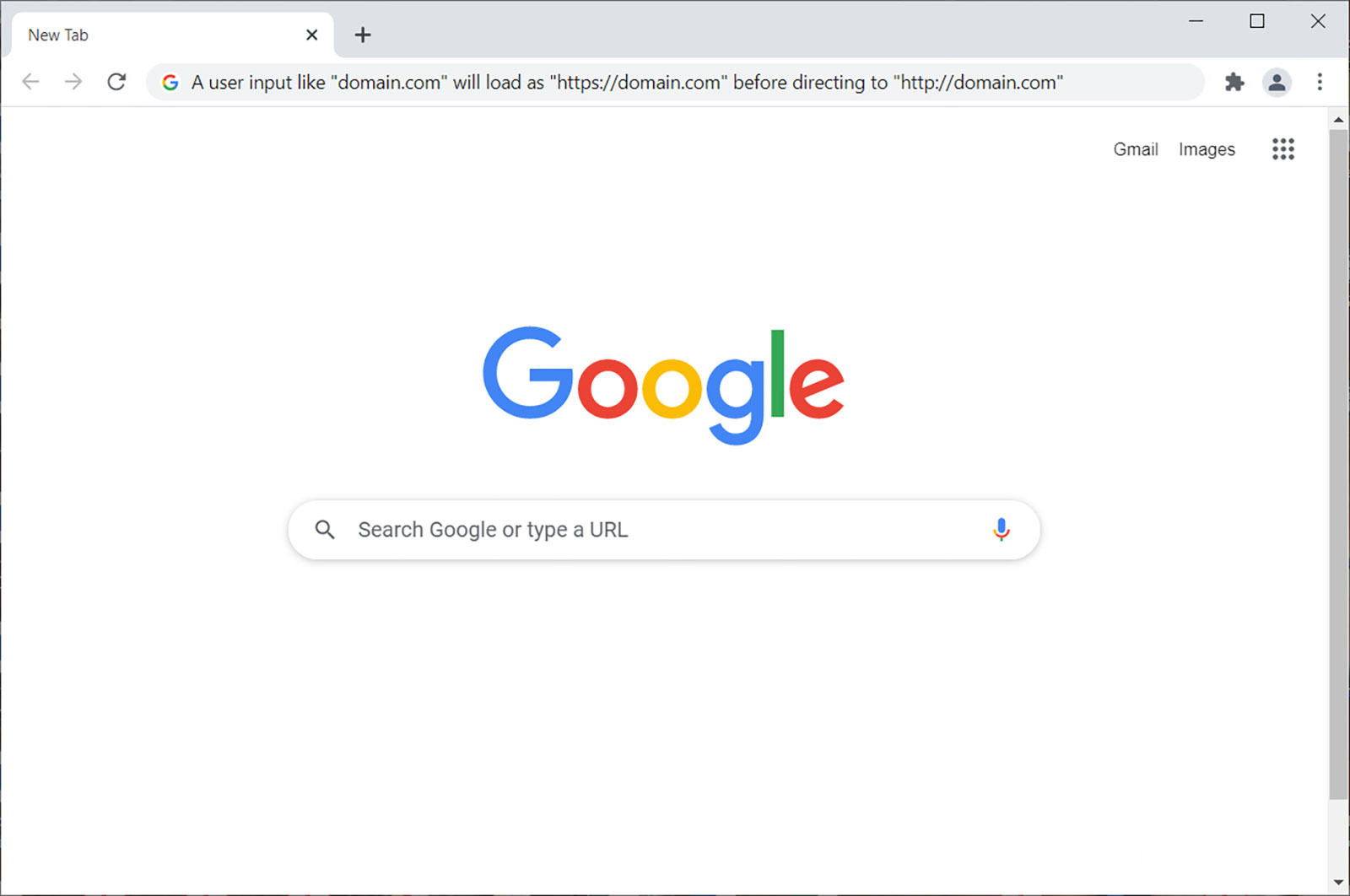
Google Chrome version 90 will default to HTTPS for incomplete URLS. For example, Chrome will load “https://domain.com” when a user types “domain.com.” (And if the HTTPS fails because a site lacks SSL/TLS, it’ll revert to using HTTP.)
It’s no secret that using HTTPS to serve up your website is faster and more secure than using the default HTTP protocol. And Google, recognizing that many browser users don’t type in complete URLs when accessing websites, decided to bridge the gap between user experience and security this year. Their latest browser update, version 90, is expected to use HTTPS by default when a user types in a website address without specifying the protocol.
In reality, this is a logical move considering that the latest data from Google’s Transparency Report shows that 95% of sites across Google already use encryption to protect their traffic. But when and why are they implementing this update? Is Chrome forcing HTTPS? And what does this change mean for your website?
Let’s hash it out.
Is Chrome Forcing HTTPS? Not Exactly…
In the Chromium Project blog’s March 23 update, Google announced many updates that they’ll be rolling out as part of their Chrome 90 update. The one in particular that we’d like to highlight is their shift to making HTTPS the default protocol when loading websites for most users.
When users manually type in URLs without specifying the scheme (http:// vs https://) in Chrome 90, the browser will try to load the site using HTTPS automatically. This means that if someone just types yoursite.com into their browser, Google will load the site as https://yoursite.com instead of the usual http://yoursite.com by default. So, instead of trying to connect first using the insecure HTTP protocol, it will make the secure HTTPS protocol the go-to instead.
Historically, Google (and other browsers) would initially try to load all web pages using HTTP by default because it was the most widely used scheme for years. In recent years, this would result in the ugly “Not Secure” warnings displaying on your site — which likely drove away some potential customers for many businesses.
But now that HTTPS is the heavyweight champion on virtually all major platforms, they’re now making the official switch to the secure protocol by default for all incomplete user queries rather than using it as a redirect.
Of course, there are a few specific exceptions that Google won’t use HTTPS for automatically — and we’ll address those items in a minute. But first, let’s talk about the advantages of Chrome using HTTPS by default.
Why This Move to HTTPS as a Default Matters
Google’s move to using HTTPS as the default method for loading websites is good because it assumes that most sites are using SSL/TLS (which they are). Will this have a big or negative impact for loading sites that aren’t using SSL/TLS certificates? Nope. Those sites will still load — it’s just that the browser is going to try loading them using HTTPS first. Then, when that fails, it’ll fall back to using HTTP to load the site.
I think Google’s likely doing this for a few key reasons:
- They assume that Chrome users want to keep their data secure. Regardless of whether users bother to type “HTTPS” as part of the web address, Google assumes that they want to use keep their data secure using encryption. (That would be a good assumption on Google’s part considering that insecure connections can result in costly data breaches.)
- Google says security is one of their top priorities. According to their Transparency Report, “We believe that strong encryption is fundamental to the safety and security of all users of the web. Thus, we’re working to support encryption in all of our products and services.”
- 95% of web traffic already uses HTTPS. Considering that the overwhelming majority of web traffic relies on HTTPS, connecting to HTTPS first just makes sense. It’s faster to try to connect with the protocol that’s most likely to succeed rather than trying HTTP first and waiting for the server to redirect to HTTPS afterward.
This move by the tech giant is a positive one that benefits everyone except the cybercriminals who want to exploit us.

Manage Digital Certificates like a Boss
14 Certificate Management Best Practices to keep your organization running, secure and fully-compliant.
Defaulting to HTTPS Automatically Improves Site Security and User Data Privacy
Cybercriminals use man-in-the-middle attacks to intercept data while it’s in transit between users’ browsers and your web server. When data transmits via HTTP, it’s moving in plaintext format that bad guys can intercept, read, modify or steal. Depending on the types of data they get their hands on, bad guys can use this information to carry out identity theft, financial fraud, or a variety of other cybercrimes.
But when you use HTTPS, you’re protecting that data using encryption so that no one but your intended party can access the readable information. You’re also asserting your organizational identity as well at the beginning of the connection so that users’ clients know that they’re connecting to your legitimate site. Here’s a quick look at what HTTPS does:
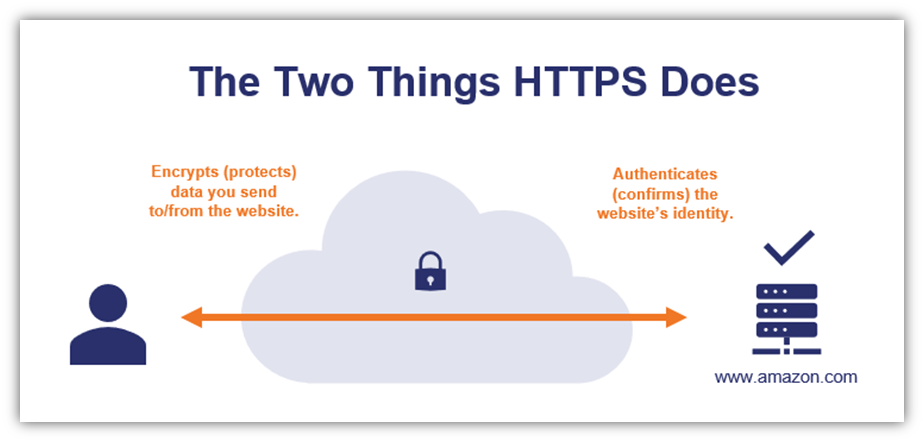
We’re not going to get into all of the details about HTTPS here. (That’s another big topic!) If you want to read more about how HTTPS works from a technical perspective, check out my colleague’s blog that really dives in on the topic.
Connecting via HTTPS Automatically Improves Site Load Speeds
By opting to load websites first using the secure scheme right off the bat, Chrome eliminates an unnecessary step for HTTPS-enabled websites — waiting for the server to redirect from HTTP to HTTPS. Using HTTPS to load HTTPS-enabled sites results in faster initial load speeds, which makes for a better user experience.
Now, what does this mean for websites that don’t yet support HTTPS? The browser will try to load the website using HTTPS by default. But when that doesn’t work, it will redirect back to HTTP. This process will kick in regardless of why HTTPS connection failed — no SSL/TLS certificate installed on your website, server misconfigurations, or other issues throwing up SSL certificate errors.
Of Course, There Are Exceptions to the Rule…
It’s important to note that Google isn’t implementing this HTTPS-by-default move unilaterally; they’ll do it in most but not all cases. In some situations, the browser will still default to use HTTP when loading specific items:
- Single-label domains,
- Reserved hostnames (examples they gave include localhost/ and test/), and
- IP addresses.
In the case of the first two items, they’re not public parts of the internet as they exist on your local network and on your computer, respectively. As such, they wouldn’t have publicly trusted SSL certificates — only self-signed or private SSL certificates, which wouldn’t matter here since they wouldn’t be trusted by default anyhow. And while IP addresses can be secured using SSL/TLS certificates, it’s infrequently done and some CAs don’t issue certificates for IP addresses.
But what if you want to redirect Google and other major browsers to always load your public-facing website using HTTPS (even if the http:// protocol is provided in the link or user input)? There are a few ways you can do that.
How to Tell Clients to Load Your Website Using HTTPS By Default
Of course, Google’s update isn’t the only way to use HTTPS for all of your site’s incoming traffic. If you have a valid and properly configured SSL/TLS certificate installed on your server, then there are a few ways you’ve been able to achieve this:
Via URL Redirect
You can configure your web server to automatically redirect all HTTP URLs to the same URL but using HTTPS instead. This is a simple, foolproof way to ensure that users end up on the HTTPS version of your website.
HTTP strict transport security, or HSTS for short, is another way that site owners can force browsers to use secure HTTPS connections to load their websites. When a browser visits an HSTS-enabled site for the first time, it will receive the header information and know that it has to load the site using a secure, encrypted connection.
Historically, this presented a big catch-22. In order for a client to know it’s always supposed to connect using a secure connection, it first must download the header. But for the site to download the header, it first has to connect using an insecure connection. Thankfully, there’s a way to avoid this issue…
Adding Your Site to the HSTS Preload List
The HSTS preload list is a record of preloaded websites that tells browsers which sites use HSTS. All major browsers, including Chrome, consult this list when loading websites for the first time. And since they know ahead of time that specific sites have HSTS enabled, then they know to only make secure connections with those sites.
Last year, the U.S. government announced its intention to start adding new .gov domains to the HSTS preload list starting in September 2020.
But what if you don’t have an SSL/TLS enabled on your site? If your site doesn’t have an SSL/TLS certificate yet, then now’s a great time to get one. In addition to securing your data, business and extended validation SSL/TLS certificates also help you assert your site’s organizational identity. This lets users know your site is legitimate and that they can trust it with their sensitive data.
And since Chrome is defaulting to loading almost all websites via HTTPS in version 90, it means that sites using HTTP will load slower because they’ll require a redirect from HTTPS to HTTP.
When Will the Chrome HTTPS Update Roll Out?
Techradar reports that Google tested this functionality with select Chrome Beta users via their version 89 update, which rolled out earlier this year. However, Google’s Chrome Platform Status page says that the “stable” (full) version of Chrome 90 was expected to roll out to the public on Tuesday, April 13, 2021. (The Chrome Beta 90 is available for Windows and Android users.) However, this was delayed, according to Google Developer Advocate Pete LePage, who says it should be out “shortly”:
I was getting ready to publish this article yesterday (April 15) to state that the update still hadn’t rolled out. I checked the browser first thing and saw there was no update available to my version 89 Chrome. So, I updated the article draft. But just before I was going to press the “Publish” button, I decided to check the browser again and, low and behold, my Chrome browser updated then to version 90. Great! So, I decided to try testing the functionality to make sure it would load websites using HTTPS by default.
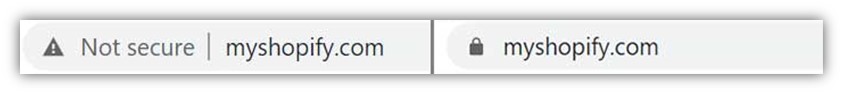
The interesting part, though, is that the HTTPS functionality update didn’t seem to roll out with it (or, at least, it didn’t appear to be enabled). So, I tested multiple websites by manually typing in a few domains without specifying “HTTPS” and they still loaded using the insecure HTTP protocol automatically (although there are HTTPS versions of those sites available when you specify “HTTPS” when manually typing those URLs). I asked a couple of colleagues to test some URLs as well in their Chrome 90 browsers and they had the same results: it defaults to HTTP instead of HTTPS.
Here are two examples that I tested:
Chrome HTTPS Update: Chrome 90 to Use HTTPS for Incomplete URLs
