
Most of us take Secured Sockets Layer (SSL) and Transport Layer Security (TLS) for granted, but over time the use of SSL and TLS certificates has dramatically changed. Once, only websites that handled secure transactions provided protection with an SSL certificate. Now search engines demand everything is protected with certificates.
Because attackers have used weaknesses in SSL to gain access to credentials, we have deprecated insecure SSL protocols in favor of more secure ones. Many of you likely became aware of the weakness in SSL when the POODLE vulnerability was first disclosed. “Padding Oracle On Downgraded Legacy Encryption” revealed a flaw in how SSL 3.0 handles block cipher mode padding. As noted in the CISA notification:
“While SSL 3.0 is an old encryption standard and has generally been replaced by TLS, most SSL/TLS implementations remain backwards compatible with SSL 3.0 to interoperate with legacy systems in the interest of a smooth user experience. Even if a client and server both support a version of TLS the SSL/TLS protocol suite allows for protocol version negotiation (being referred to as the “downgrade dance” in other reporting). The POODLE attack leverages the fact that when a secure connection attempt fails, servers will fall back to older protocols such as SSL 3.0. An attacker who can trigger a connection failure can then force the use of SSL 3.0 and attempt the new attack.”
Before POODLE, there was BEAST, an SSL attack that enables a “man-in-the-middle (MITM) attack to obtain plaintext HTTP headers via a blockwise chosen boundary attack (BCBA) on an HTTPS session,” according to its CVE description. For both SSL attacks the recommended solution was to move to more secure cypher suites. More SSL attacks include DROWN and HeartBleed.
Here are some tips to minimize the risks associates with SSL and TLS certificates:
Review SSL protocols
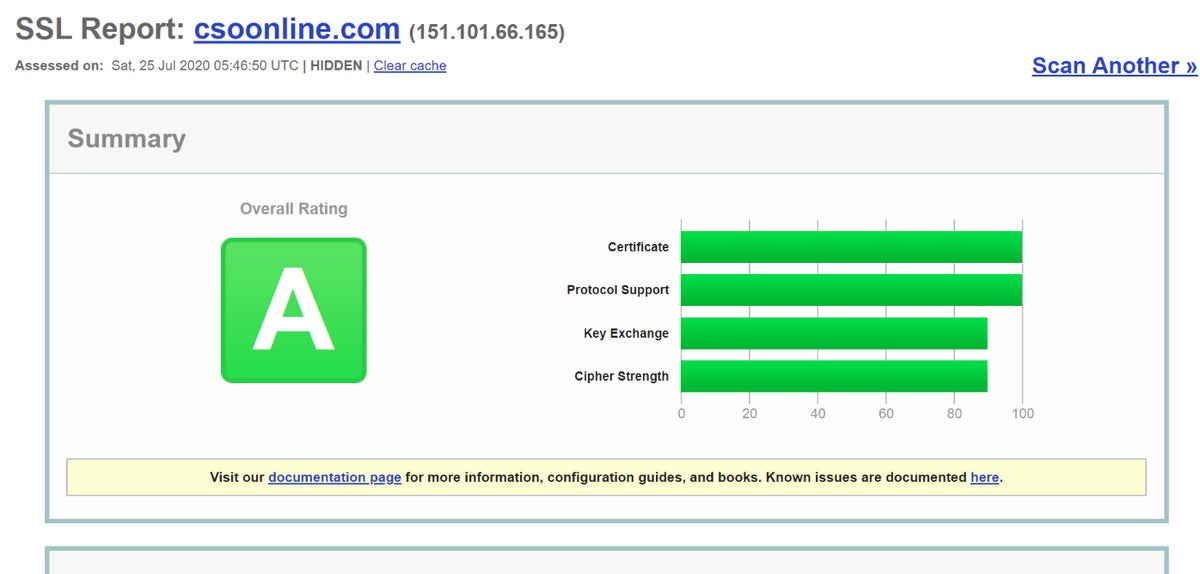
Several tools allow you to review what SSL protocols you expose to your internal and external users, but one of the easiest is SSL Server Test. Enter the website url that you wish to test and it will come back with a score card that shows where your weaknesses are.
 Susan Bradley
Susan BradleySSL Server Test reviews your SSL certifications
Aim for an “A” score. Even if you receive an A, review if you need to take actions in the future to better support secure protocols.
Review SSL settings
IISCrypto is a good tool to use to review your website for best practices. It allows you to review and change your certificate settings to make them more secure—for example, to automatically disable insecure protocols such as SSL 2.0, 3.0, MD5 and 3DES. The tool also provides you with a review for PCI compliance or general best practices. Take the time now to review your certificate support throughout your entire firm, and also review your SSL cert renewal process.
Review your SSL certification renewal process
Once upon a time you could renew SSL certs used on your websites and other implementations for years. Now you can’t obtain a certificate for longer than 398 days. Why so short? Apple has decided that it won’t let its Safari browser trust any SSL certificate older than 365 days plus the renewal grace period.
Ensure that you have a process or procedure for managing and tracking SSL cert expiration dates. You might decide to have a staggered renewal process, or an automatic process set up to renew and rekey certificates. One of the free SSL certificate vendors, Let’s Encrypt, provides SSL certificates for only 90 days. That might seem excessively short, but Let’s Encrypt provides a process to automatically renew these certificates.
Don’t forget certs for Windows and applications
Applications often use SSL and TLS certificates as well. If you are still using TLS 1.0 and 1.1, the COVID-19 pandemic has impacted plans to deprecate these two protocols. For Office 365, Microsoft planned to phase out TLS 1.0 and 1.1 in early 2020, but they decided to push that off until October 2020.
For older platforms, look for patches to provide support for later TLS protocols. For example, if you still use Windows 7, several patches support TLS 2.0 on RDP, WinHTTP and .NET so you can disable the weaker protocols. Older SharePoint platforms need patching and tweaks to support TLS 1.2. Determine for each older platform if they can support TLS 1.2 before you can disable the protocols and not impact your business needs. For example, the Disable TLS 1.0/1.1 in Skype for Business Server 2015 documentation page lists applications that will not work after TLS 1.0 and 1.1 are disabled.
In 2017 Microsoft prepared a whitepaper called “Solving the TLS 1.0 Problem” that outlined the TLS 1.0 deprecation plan:
- Perform code analysis to find/fix hardcoded instances of TLS 1.0 (or instances of older TLS/SSL versions).
- Scan network endpoints and analyze traffic to identify operating systems using TLS 1.0 or older protocols.
- Perform full regression testing through your entire application stack with TLS 1.0 disabled.
- Migrate legacy operating systems and development libraries/frameworks to versions capable of negotiating TLS 1.2.
- Perform compatibility testing across operating systems used by your business to identify TLS 1.2 support issues.
- Coordinate with your business partners and customers to notify them of your move to deprecate TLS 1.0.
- Understand which clients may not interoperate by disabling TLS 1.0.
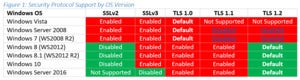
As noted in the whitepaper, the following protocols are supported by the various operating systems:
 Susan Bradley
Susan BradleyFor each operating system, the version of SSL will connect with the lowest supported and enabled protocol. To connect with TLS 1.2 as a default you will need to disable the lower protocols. You can test your client implementations on the Qualys site.
If your network requires FIPS Mode but you also want to deprecate TLS 1.0/1.1, take the following steps:
- Configure TLS versions via the registry by setting “Enabled” to zero for the unwanted TLS versions.
- Disable Curve 25519 (Server 2016 only) via Group Policy or PowerShell.
- Disable any cipher suites using algorithms that aren’t allowed by the relevant FIPS publication. For Server 2016 (assuming the default settings are in effect) this is means disabling RC4, PSK and NULL ciphers.
Review how your network and computer assets will be impacted by upcoming changes and enforcement of TLS 1.3.
Copyright © 2020 IDG Communications, Inc.
4 best practices for managing and tracking SSL and TLS certificates
