
How well you manage and secure your secure shell key lifecycle in part determines the security of your network and other IT environments. Here are several SSH key management best practices that will help you get started
SSH key management is an oft-overlooked element of identity and access management (IAM). Here at Hashed Out, we typically focus on public key infrastructure (PKI)-based forms of authentication and digital identity because that’s our specialty and area of expertise. However, we have to acknowledge that secure shell (SSH), which is something virtually all companies use in some capacity, also needs some love in terms of coverage every once in a while.
This is why we’ve decided to tackle an article that addresses some of the most important SSH key management best practices for your business. But what are the top 14 SSH key management best practices you need to implement now and how do they benefit your organization?
Let’s hash it out.
What Is SSH Key Management? The Role of SSH Keys in Identity & Access Management
Before we jump right into defining SSH key management, let’s first quickly rehash what secure shell is, what SSH keys are, and how organizations use them for user-friendly authentication and increased data security.
What Is SSH and What Does It Do?
SSH, which stands for secure shell, is a cryptographic network protocol that allows secure authentication and data communications between two devices via open channels. SSH is critical for network and general system administration (such as for managing firewalls, networks, servers, etc.). As something that’s literally built into Unix and Linux servers, it’s a client-server model system that aims to secure remote access between users and critical systems via insecure connections.
More simply stated, SSH is the numero uno system that IT admins use to log in to servers and other Linux machines to manage them remotely. The way it works is when authorized users log in to a secure shell environment to authenticate, their devices gain access to one or more devices or resources within your secure IT environment. As such, it’s easy to see how SSH authentication plays a critical role in your organization’s identity and access management processes.
When you use SSH to log in using admin root access, you have complete control over the machine. SSH access serves as your key to your kingdom, giving you control of all commands and files. So, as you can imagine, protecting that kind of privileged access through proper SSH key management is crucial to your organization’s security. (Going out a limb here to say that SSH security is important to you since you’re still here and have read this far, at least…)
SSH Authentication (and Where SSH Keys Fit Into the Picture)
SSH authentication can occur in a few different ways. However, the two we’re going to focus on today are password- and SSH-key-based authentication methods. And our primary focus, as your can probably guess from this article’s title, is going to focus on SSH key management best practices specifically.
- Password-based SSH authentication occurs when a user manually enters their login credentials to access a secure resource. An example of this is when one of your coworkers enters their individual username and password into a login field to access a file in, say, Amazon Web Service’s Elastic Computing Cloud (AWS EC2).
- SSH-key-based authentication allows a user to authenticate automatically using a cryptographic keypair. These keypairs, which consist of private and public keys, are used to authenticate users (their devices) and hosts. Basically, you use the local machine that has the private key to authenticate to AWS once. After that, all SSH interactions between the two devices will rely on the key pair for authentication.
In a nutshell, SSH keys are another form of machine identity and authentication. They enable your organization’s authorized, authenticated users to access critical systems to perform their jobs. But SSH keys, unlike traditional PKI keys that we use with X.509 digital certificates, don’t have public keys that are signed by a certificate authority (i.e. certification authority or CA) like DigiCert or Sectigo. (In SSL, you generate your SSL keys yourself through the CSR process, and the public key is what the CA signs as part of your certificate.) And even though SSH authentication involves a process that’s similar to the SSL/TLS handshake, its authentication process isn’t as complex.
Related: Secure Your Domain & Sub-Domains with a RapidSSL Wildcard Certificate.
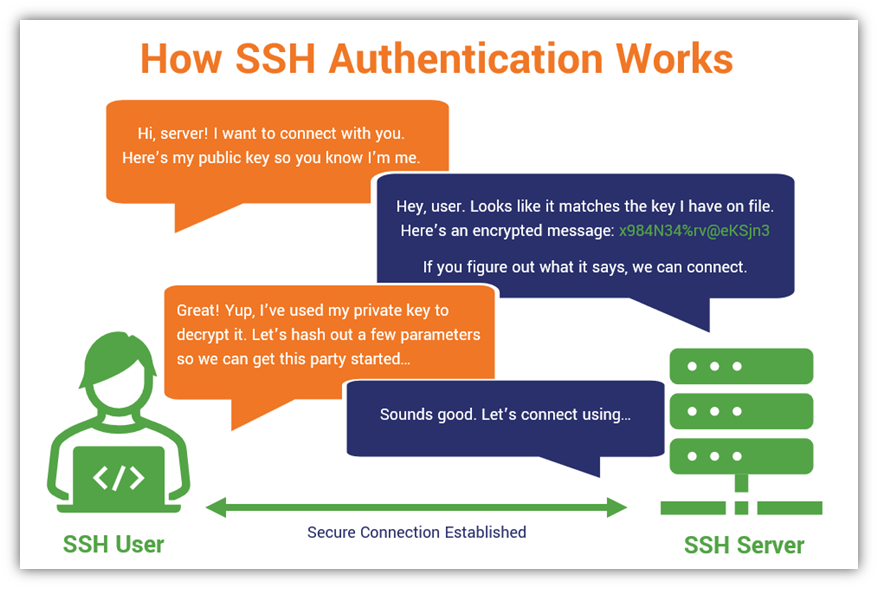
Here’s a quick (and simplified) overview of how SSH authentication works:
But when comparing password- and key-based SSH authentication methods, which option is better or more secure? EdgeScan’s 2021 Vulnerability Statistics Report shows that some of the biggest growths in terms of exposure for organizations in 2020 relate to the use of insecure SSH credentials.
“Remote desktop (RDP) and Secure Shell (SSH) exposure increased by around 40%, likely due to the increase in remote working due to covid-19. RDP (and similar services) are easy and commonly used avenues for brute force or credential stuffing attacks, against weak user credentials.”
EdgeScan’s report shows that in their sample of one million public-facing endpoints’ exposed services, SSH represented 3.8% (38,000) in terms of “remote system login and management.”
When properly managed, SSH keys offer an authentication method that’s more secure than using traditional login credentials alone. Why? Because keys are resistant to brute force attacks. But the security and effectiveness of those keys depend on how well your organization keeps track of them. This is where following SSH key management best practices comes into play.
SSH Key Management — It’s How You Control the Keys to Your Kingdom
SSH key management is the combination of policies, processes and tools that enable you to protect and manage those digital key pairs. Secure shell keys allow users to authenticate themselves to your network, servers, or other systems and securely share files without continually logging in using a username and password.
Some of the benefits of effective SSH key management include:
- Having full visibility into your access keys at all times (this helps you to ensure each is protected from theft).
- Knowing that you’re not accidentally re-using keys across systems and users (yeah, this can happen).
- Ensuring you don’t get locked out of a server or system if you lose an access key (accidents happen).
- Having the ability to immediately change or revoke access for employees (for example, when someone leaves the company).
- Being able to change or revoke access if a key becomes compromised (you’ve gotta act quickly in this situation).
Much like PKI key management, successful SSH key management revolves around how well you can protect and keep track of your organization’s public and private keys. This means using effective methods to generate, store, rotate, revoke, and use them in ways that keep them out of the hands of cybercriminals and other unauthorized users. This requires processes that ensure proper SSH key provisioning, terminations, and monitoring across all of your IT environments.
And this can be tricky, considering that without proper access management and approval processes in place, users can simply issue themselves access privileged access to your most critical systems. This is why having a strong SSH key management program in place is essential. It’s also why SSH key management should be part of your access and IT risk management and remediation processes, policies and strategies.
SSH Key Mismanagement Leaves You Vulnerable and Non-Compliant with Industry Regulations
You should understand by now that mismanaging your SSH keys leaves your organization at risk of credential compromise, data theft, and data breaches, but did you know it also makes you non-compliant with some industry regulations? Many well-known regulations — HIPAA, GDPR, PCI DSS — all require data security and privacy protections. Some of these requirements relate to managing access to that data, which implies or specifies the use of cryptographic keys such as SSH keys.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA’s Security Rule requires covered organizations to implement role-based access measures to protect electronic protected health information (ePHI) data when it’s in use, in transit, and at rest. This is something that SSH key management plays a role in.
Payment Card Industry Data Security Standards (PCI DSS)
PCI DSS Requirement 4 specifies that covered organizations must use encrypted transmissions to transmit cardholder data over open networks. This requires the use of cryptographic processes and components like public-private keypairs.
PCI DSS Testing procedure 2.3 requires the use of “strong cryptography” for all non-console administrative access. According to the PCI DSS guidance specified in 2.3c: “To be considered ‘strong cryptography,’ industry recognized protocols with appropriate key strengths and key management should be in place as applicable for the type of technology in use[.]”
General Data Protection Regulation (GDPR)
The European Union’s GDPR requires the secure processing of covered personal data. GDPR Article 32 specifies the use of “appropriate technical and organisational measures,” which include data encryption and secure access to that data. (This includes the use of public key encryption methods to secure access.)
Needless to say, if bad guys manage to get their hands on your employees’ SSH keys, it can lead to many dire and costly consequences. This is why SSH key management should be a priority for every business regardless of size.
14 SSH Key Management Best Practices You Need to Implement Now
Research from Acunetix’s 2020 Web Application Vulnerability Report shows that 15.5% of the 5,000 scan targets they analyzed had SSH-related vulnerabilities. A large part of this is due to SSH key mismanagement. That’s because the security of SSH keys is only as good as the SSH key management and auditing practices you implement.

Effectively managing your SSH keys entails knowing:
- The precise number of SSH keys that exist within your IT environment,
- When and how each key is used and which system(s) it has access to,
- How old each key is and when you need to replace it, and
- How to safely generate, store, revoke, and remove the keys within your network and overall IT environment.
The National Institute of Science and Technology (NIST) provides in-depth guidance for SSH access management in their interagency report 7966 (NISTIR 7966). They cover many vulnerabilities, including:
- SSH implementation issues,
- Access control configuration issues,
- Unintended SSH key usage, and
- Unknown or unaudited active keys (and the risks associated with them).
However, there’s a lot of material to cover there and, frankly, we don’t think you’re here to get into the nitty-gritty of all of that now. That’s why we’re going to take a bit more of a high-level approach to SSH key management in this article.
So, without further ado, let’s break down the 14 SSH key management best practices you can put to work now to protect and manage access to your organization’s IT environments and data. These best…
