
We all know that HTTPS = secure. But do you know how HTTPS works under the hood? Let’s take a look at how HTTPS works to make the internet safer for all of us…
95% of webpages viewed in the US are viewed using HTTPS. (That’s according to Google Chrome user data via the Google Transparency report.) Other countries also overwhelmingly use HTTPS URLs — 93% in Germany, 85% in Japan, and 85% in India. HTTPS has been adopted worldwide as the preferred protocol for most websites. But just how does HTTPS work and what does it do?
If you’re reading this article, you probably already know that the “S” in HTTPS means secure. You’ve likely looked for https:// (or a padlock icon) at the beginning of a URL to confirm it was secure before entering your credit card details online.
But what does HTTPS do for the average internet user? And how does HTTPS work in a more technical sense?
Let’s hash it out.
How HTTPS works is actually a pretty big topic, so we’ll break it down into several sections–starting with the basics. If you’re already somewhat familiar with HTTPS and want to skip around, you can use this table of contents to jump to the part that interests you.
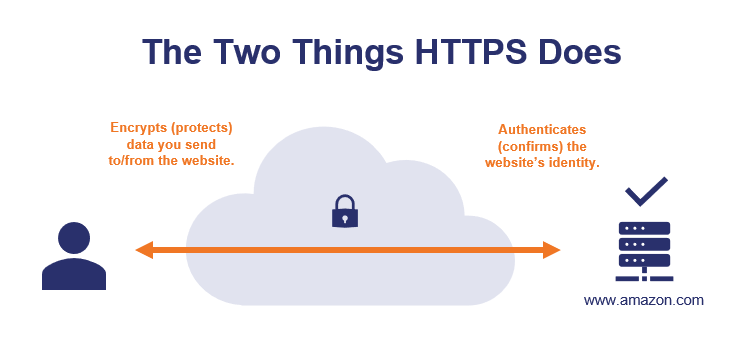
When you go to a website that starts with https://, that tells you two very specific things:
- A third party has authenticated the website. The website has been authenticated to verify it is the website it claims to be — if your browser bar says https://www.amazon.com, you can be confident that you’re actually on amazon.com.
- The site uses encryption. Data you send to/from the website is encrypted so other parties can’t see/steal it—you can submit credit card numbers or other sensitive data and know that nobody can intercept your info while it’s making the trip to amazon.com.
Important note about terminology: you’ll hear the terms “SSL” and “TLS” used in conjunction with HTTPS. A few quick facts will make these terms easier to keep straight:
- Secure sockets layer (SSL) and transport layer security (TLS) refer to the type of secure connection that HTTPS uses for communication between a web browser and web server.
- Technically speaking, SSL is an older technology that was deprecated and replaced with TLS.
- Practically speaking, most people use the terms interchangeably. That’s why you’ll sometimes see us use “SSL/TLS” or “SSL/TLS Certificate.”
- SSL/TLS and HTTPS go together like dirt and grass. You can’t grow grass without dirt, and you can’t have HTTPS without SSL/TLS.
Let’s dig a little deeper into how HTTPS works to provide these two security benefits…
HTTPS Authentication Ensures You’re Connected to the Correct Website (And That’s More Important Than It Sounds)
As mentioned, the first thing that HTTPS does is authenticate the website to verify that your browser is connected to the correct website. If you typed in amazon.com, your browser uses HTTPS to ensure that the website you’re connected to is the real amazon.com (not a fake website run by a hacker in a back alley in San Fransokyo).
Why HTTPS Authentication Is Important
Now, you may be wondering why this is necessary — “can’t I just look at the URL in my browser’s address bar?”
If it says amazon.com and it looks like amazon.com, it must be amazon.com, right? Not necessarily.

Your browser’s address bar is always a good place to check, but it’s not foolproof — it’s possible that you could type http://www.amazon.com into your browser’s address bar and get a website that looks like Amazon.com… but is actually a fake website run by a hacker.
Hackers can use DNS poisoning, malware, or other attack methods so your browser invisibly connects to the wrong website server. So while it looks like you’re connecting to a legitimate URL in your browser bar, you’re actually on a fake website run by a hacker.
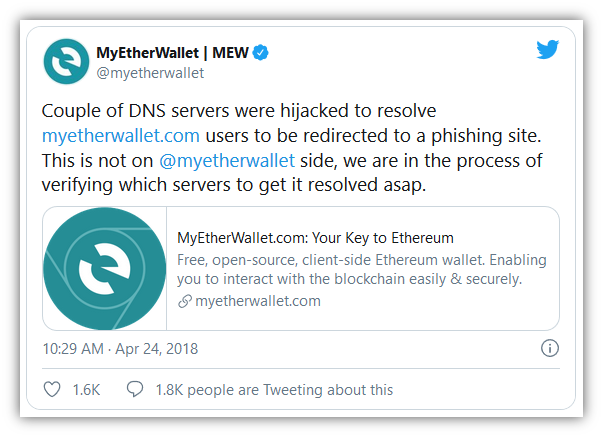
Let’s consider a real-life example. Hackers used DNS poisoning to take a legitimate domain name and point visitors to a fake website where they stole $150K from MyEtherWallet users.
How Do DNS Attacks Like This Work?
First of all, we need to briefly discuss how your computer actually connects to websites. When you type in amazon.com, your computer doesn’t actually understand “amazon.com” as an address it can connect to. Amazon.com is the human-readable address, the actual address your computer connects to is the IP address (which looks like this: 176.32.103.205). Your computer needs to lookup amazon.com’s IP address using the DNS system before it can connect to the amazon.com web server.
Here’s a simplified representation of the process:
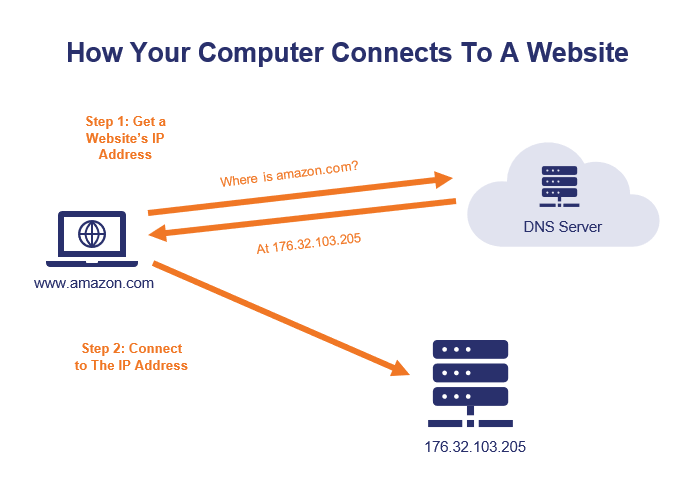
When you visit a website, your computer uses the DNS system to get the IP address of the website you’re trying to visit. Your computer is actually connecting to an IP address, not to an address like amazon.com. In a DNS poisoning attack, your computer is given an incorrect IP address, which means that your computer connects you to the wrong server. Your computer thinks it’s amazon.com and you think it’s amazon.com, but it’s not.
Want to read further? If you’d like to read the in-depth version of how DNS poisoning attacks work, read our guide on DNS Poisoning Attacks.
The good news is that HTTPS is an effective defense against hacker tricks like DNS poisoning. How? Let’s dive into how HTTPS works to ensure that you’re on the correct website.
How HTTPS Authentication Works
So, how does HTTPS ensure that you’re connected to the correct website?
Your browser uses an SSL/TLS certificate and the certificate authority that issued it to authenticate each HTTPS website that you visit. Here’s how it works…
Step 1: Getting a Certificate
First, the website needs to have an SSL certificate issued by a publicly trusted certificate authority. An SSL certificate is a lot like a passport — but it’s for websites, not people. An SSL certificate includes details such as:
- The website’s URL(s),
- A public key (which is linked to a private key only possessed by the website),
- The certificate authority that issued the certificate,
- The certificate’s expiration date, and
- The legal organization that runs the website (optional).
To get a valid SSL certificate, the website owner will have to go through a few steps:
- Generate a public key and a private key (more on how they’re use later).
- Go through a specific process to prove to the certificate authority that they’re the actual owner of the website.
- In the case of OV and EV SSL certificates, the website owner also has to prove that they’re an actual, legally registered organization.
Once those steps are completed, the certificate authority issues an SSL certificate to the website owner. This certificate is installed on the web server and is automatically provided every time someone visits the website via an https:// URL.
Step 2: “Passport, Please!”
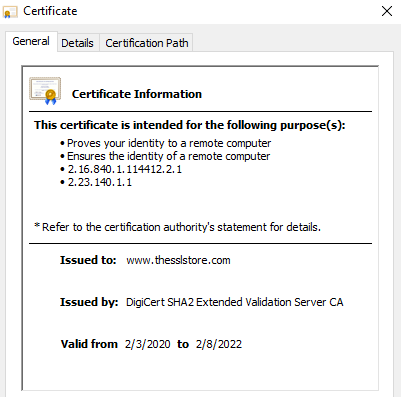
When you visit an HTTPS website, the website sends its SSL/TLS certificate to your web browser. Let’s use our website as an example. If you click on the padlock in your browser, then click to view certificate details, you can see our website’s certificate and the information it includes.
If you open the Details tab, you’ll see more information about the website and the organization that runs it, like this:
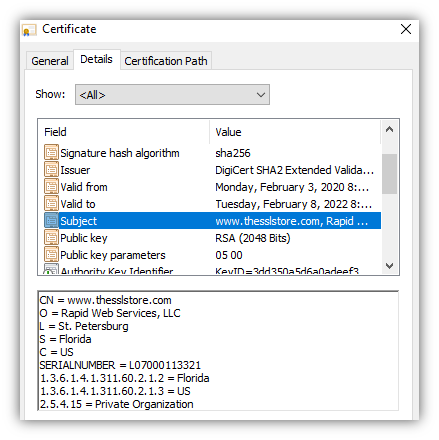
Some websites (like ours) have certificates that also show their company details (such as company name, location, etc.). These are called organization validation (OV) or extended validation (EV) certificates. The company details are also verified, so you can be 100% confident you know exactly who is running the website you’re on.
Step 3: Verifying the Certificate
Now we come to the critical step — verifying the website’s SSL certificate. Just because the website presents an SSL certificate doesn’t mean that your browser should trust it. After all, as Albert Einstein famously said:

Fortunately, your browser has a way it can verify the website’s SSL certificate to ensure it’s accurate and not a fake. Specifically, your browser will verify whether:
- The website’s SSL certificate was issued by a certificate authority on the browser’s trusted list. (The browser uses the certificate authority’s digital signature to instantly confirm that the certificate authority issued the website’s certificate.)
- The SSL certificate is valid for the website domain/URL you’re visiting.
- The SSL certificate is currently valid and has not expired or been revoked.
If the certificate passes those checks, your browser will display the website, along with https:// and a padlock next to the URL.
If you look at our website’s certificate, you’ll see that it is issued by DigiCert. Our website’s certificate includes a digital signature from DigiCert that your browser can use to verify the certificate is a valid and was issued by DigiCert.
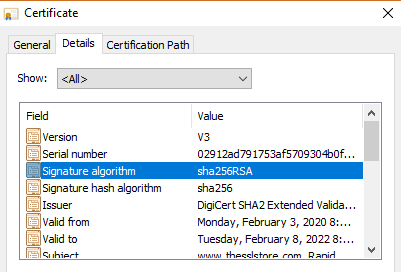
We’ll dive into more technical details later, but the main point for now is: your browser checks each website’s HTTPS credentials, just like airport authorities check your passport before you can board an airplane.
HTTPS Encryption Ensures Others Can’t Spy on Your Communications
The second thing that HTTPS does is encrypt all information that’s sent between you and the website you’re visiting. This ensures that nobody (other than you and the website you’re connected to) can read your data as it’s sent across the internet.
Let’s use amazon.com again as an example. Say, you’re shopping for a lovely Nicholas Cage sequin pillow:
You want to place your order online, but security and privacy are very important to you. You don’t want anyone to steal your credit card details, and perhaps more importantly you don’t want anyone to know that you sleep with a Nicholas Cage pillow on your bed. (I won’t judge you!)
Because amazon.com uses HTTPS, that means all data sent to/from amazon.com is encrypted before being sent. Let’s a take a brief look at how HTTPS works on the encryption side…
How HTTPS Encryption Works
In order to buy that Nicholas Cage pillow, you need to enter your credit card details:
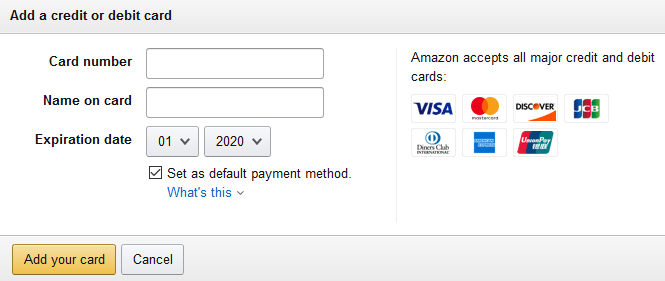
When you enter your credit card numbers in the above field and click “Add your card,” your credit card details are submitted to Amazon.com. But first, your browser will encrypt the data.
This means that:
- The data is encrypted using an encryption key so only Amazon can unlock (decrypt) the data, and
- Your credit card (and other data) will look like gibberish to anyone who doesn’t have the decryption key.
The data will travel across the internet in its encrypted (unreadable) state. Once it reaches amazon.com, Amazon would decrypt the data so it can read your credit card number to process your payment:
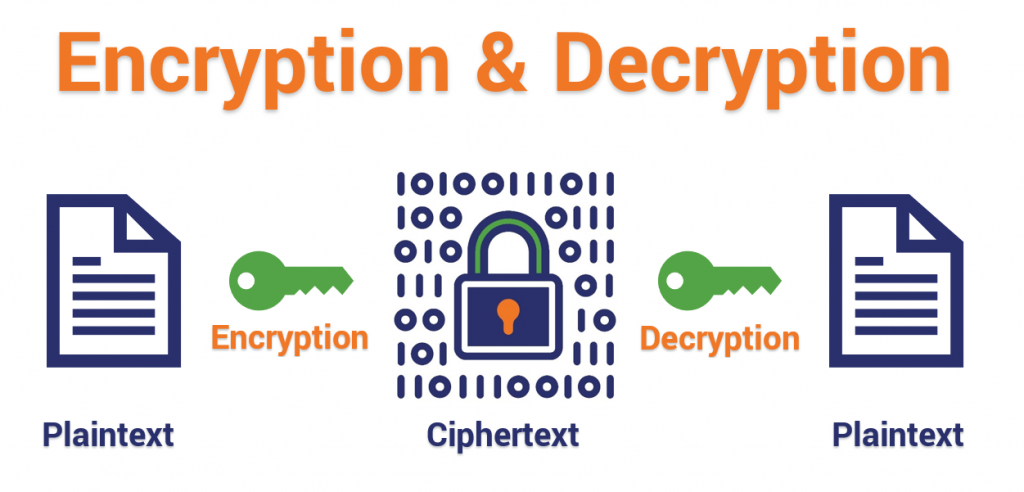
You might be wondering — what exactly is encrypted text (aka ciphertext)? Here’s an example, showing actual encrypted data (as you can see, it’s gibberish unless you have the decryption key to read it):
| Data you enter: | Encrypted data (ciphertext) that is sent over the internet: | After Amazon decrypts the data: |
| 1234123412341243 | MHecmaRMbHdU8KRzY0h+n7n9 A3yR1ZJOBbY6PuEYRH0= | 1234123412341243 |
Encryption makes it safe to send encrypted data across the internet.
What HTTPS Encryption Doesn’t Do
Here’s one important distinction to make — HTTPS encryption only protects your data while it’s traveling to the website (i.e. amazon.com in this case). Once the data reaches the website, it’ll be decrypted and then…
